Cisco CyberOps Associate 28.4.13 Lab – Incident Handling
Scenario 1: Worm and Distributed Denial of Service (DDoS) Agent Infestation
Study the following scenario and discuss and determine the incident response handling questions that should be asked at each stage of the incident response process. Consider the details of the organization and the CSIRC when formulating your questions.
This scenario is about a small, family-owned investment firm. The organization has only one location and less than 100 employees. On a Tuesday morning, a new worm is released; it spreads itself through removable media, and it can copy itself to open Windows shares. When the worm infects a host, it installs a DDoS agent. It was several hours after the worm started to spread before antivirus signatures became available. The organization had already incurred widespread infections. The investment firm has hired a small team of security experts who often use the diamond model of security incident handling.
Answer
The first important thing to note in this scenario is the attribution of malware infestation to DDoS. DDoS is often an external attempt to overwhelm an infrastructure. Hence, it is safe to assume that all the infected hosts become botnets and are reporting to a CnC.
That said, the aim of incident response is to limit the impact of the attack, evaluate damage caused and implement recovery procedures. According to NIST 800-61r2, the Incident Response Life Cycle contains the following:
- Preparation
- Detection and Analysis
- Containment, Eradication and Recovery
- Post incident activities
The Diamond Model of Security Incident Handling is an intrusion analysis method used to discover, develop, track, group and counter threat activities and threat actors. It is made up of the following:
- Adversary — this refers to the threat actor
- Infrastructure — the paths used to connect to the victim
- Capability — the means, tools or processes used to exploit the victim
- Victim — affected host
Using the diamond model to analyse this scenario, the following questions can be asked:
a. What hosts are affected by the malware infestation?
b. What method and tool were used to explore the victim?
c. How does the malware spread?
d. Which host was first attacked by the malware?
e. Who is/are the threat actor(s)
Using the Diamond Model to further analyse this scenario gives us the diagram below:
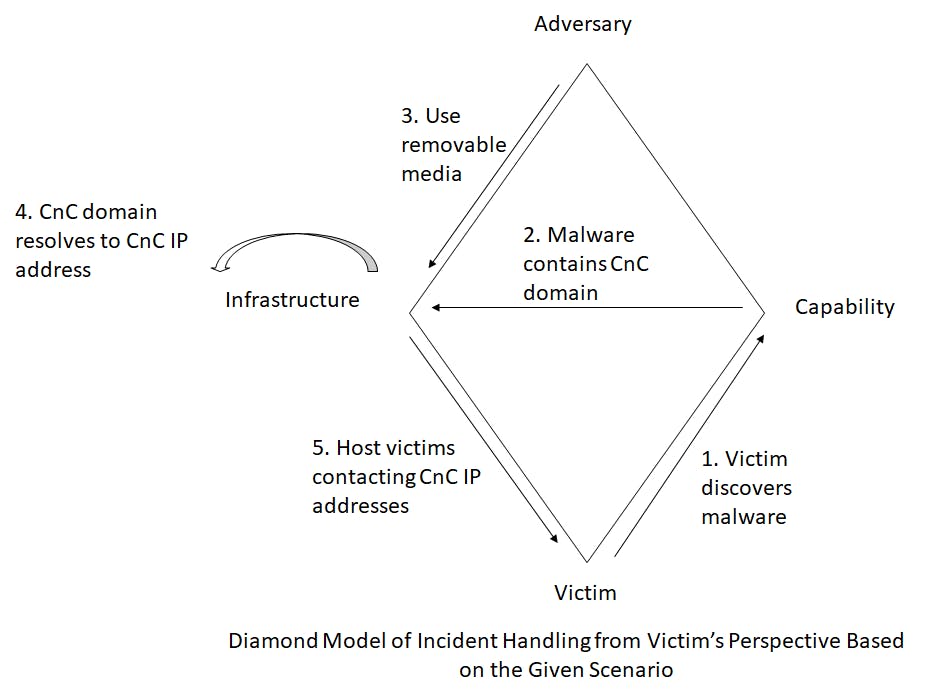
With this diamond model we have more details on the malicious activities carried out on the victim. Some of this details include the attack vector (removable media), the malware's associated IPs, such as the IPs of other affected hosts and the CnC IP which can help analyst track the threat actor. Through the model also, an analyst can gain more insight on the incident by investigating the tools and infrastructure used in the attack from incident databases. If the tool is a previously known tool, or one documented from previous attacks on other organizations, analysts can gain useful information on how the malware hides from detection or how slight modification to the chain of attack can still result in successful hacks.
There are meta-features of the diamond model that makes it more effective in Incident Handling. These are:
a. Timestamp—This indicates the start and stop time of the event. It makes grouping of events easy.
b. Phase — This refers to the steps required for the attack to be successful. Phase can be likened to the Kill Chain and can be determined based on statistical analysis of the incident.
c. Result — What the threat actor gained from the attack.
d. Direction—This depicts the direction of events across the diamond model. The direction of events in the scenario above is is denoted by a progressive numbering between (1) to (5).
e. Methodology — This classifies the event type. The methodology in the above scenario is worm infestation
f. Resources — These refers to the assets and resources used by the threat actor to launch an intrusion attack. In our given scenario, the resources associated with the intrusion are physical access to the system, malicious software and removable media.
Using the NIST Incident Response Life Cycle, some questions can be asked. These questions have been grouped under the associated stages of the Incident Response Life Cycle below:
Preparation
Questions:
a. What are the Systems and Network profiles...that is the normal and expected behaviors of the systems and networks in the organization?
b. What are the organization's asset?
c. Are there mitigation software such as an image of OS and app installation files that may be needed for recovery
Detection and Analysis
Detection
a. What is the attack vector?
b. Was there a detection indicator?
Note: In this scenario, the malware was detected by the antivirus, so it was automatic. There exists two categories for the signs of an incident. These are precursor and indicator. In this scenario, the incident sign is an indicator because the host has already been infected with a malware (DDos agent).
Analysis
a. How can the attack be validated?
Note: The answer to this may vary. However, one good way to validate the attack is to compare the incident against Network and System Profiles/ normal and expected system and network behavior.
Scope
a. What is the scope of the attack?
This entails the true extent of infestation and the degree of compromise.
Note: Given the scenario, this can be summarized as:
The attack vector is removable media. The worm spreads by itself by copying itself to open window share. The malware installs a DDos agent on infected hosts, as such they function as botnets contacting a CnC domain.
Notification
a. Has the stakeholders been notified of the incident?
Containment, Eradication and Recovery
Containment
a. What is the containment strategy?
Note: The answer to this question could vary depending on perspective. However, I would contain the attack by not unplugging compromised hosts from the network so that in case the malicious process is reporting the system behavior to CnC center, our action would not motivate the threat actor to trigger a data wipe or encryption on the target host(s). If possible, the attacker will be redirected to a sandbox to observe and document the attacker's methodology.
Eradication
a. Should we clean and remediate?
b. Should we wipe and replace?
Note: The extent of the infestation and degree of compromise would determine which of the two options above will be explored.
Recovery
a. Do we need to delete the RAM cache ?
b. Are patch and updates available ?
Note: Clean and recent backups can be used to recover hosts or they can be rebuilt with installation media.
Post-incident activity
a. What did we learn from the attack?
b. How can we prevent the similar attacks from happening in the future? Note: These two fall under lesson-based hardening.